In posting bellow we are going to demonstrate Chrome Advanced REST Client
successfully issuing REST API POST requests for creating RDO Mitaka Servers (VMs) as well as getting information about servers via GET requests.
All required HTTP Headers are configured in GUI environment as well as
body request field for servers creation.
Version of keystone API installed v2.0
Following [ 1 ] to authenticate access to OpenStack Services, you are supposed first of all to issue an authentication request to get authentication token. If the request succeeds, the server returns an authentication token.
Source keystonerc_demo on Controller or on Compute node. It doesn't
matter. Then run this cURL command to request a token:
curl -s -X POST http://192.169.142.54:5000/v2.0/tokens \
-H "Content-Type: application/json" \
-d '{"auth": {"tenantName": "'"$OS_TENANT_NAME"'", "passwordCredentials": {"username": "'"$OS_USERNAME"'", "password": "'"$OS_PASSWORD"'"}}}' \
| python -m json.tool
to get authentication token and scroll down to the bottom :-
"token": {
"audit_ids": [
"ce1JojlRSiO6TmMTDW3QNQ"
],
"expires": "2016-04-21T18:26:28Z",
"id": "0cfb3ec7a10c4f549a3dc138cf8a270a", <== X-Auth-Token
"issued_at": "2016-04-21T17:26:28.246724Z",
"tenant": {
"description": "default tenant",
"enabled": true,
"id": "1578b57cfd8d43278098c5266f64e49f", <== Demo tenant's id
"name": "demo"
}
},
"user": {
"id": "8e1e992eee474c3ab7a08ffde678e35b",
"name": "demo",
"roles": [
{
"name": "heat_stack_owner"
},
{
"name": "_member_"
}
],
"roles_links": [],
"username": "demo"
}
}
}
*****************************************************************************************************
Original request to obtain token might be issued via Chrome Advanced REST Client as well
*****************************************************************************************************

Scrolling down shows up token been returned and demo's tenant id

Required output
*****************************************************************************
Next create ssh-keypair via CLI or dashboard for particular tenant :-
*****************************************************************************
nova keypair-add oskeymitaka0417 > oskeymitaka0417.pem
chmod 600 *.pem
******************************************************************************************************
Following bellow is a couple of samples REST API POST requests starting servers as they are usually described and issued ( [ 2 ] )
******************************************************************************************************
curl -g -i -X POST http://192.169.142.54:8774/v2/1578b57cfd8d43278098c5266f64e49f/servers -H "User-Agent: python-novaclient" -H "Content-Type: application/json" -H "Accept: application/json" -H "X-Auth-Token: 0cfb3ec7a10c4f549a3dc138cf8a270a" -d '{"server": {"name": "CirrOSDevs03", "key_name" : "oskeymitaka0417", "imageRef": "2e148cd0-7dac-49a7-8a79-2efddbd83852", "flavorRef": "1", "max_count": 1, "min_count": 1, "networks": [{"uuid": "e7c90970-c304-4f51-9d65-4be42318487c"}], "security_groups": [{"name": "default"}]}}'
curl -g -i -X POST http://192.169.142. 54:8774/v2/1578b57cfd8d43278098c5266f64e49f/servers -H "User-Agent: python-novaclient" -H "Content-Type: application/json" -H "Accept: application/json" -H "X-Auth-Token: 0cfb3ec7a10c4f549a3dc138cf8a270a" -d '{"server": {"name": "VF23Devs03", "key_name" : "oskeymitaka0417", "imageRef": "5b00b1a8-30d1-4e9d-bf7d-5f1abed5173b", "flavorRef": "2", "max_count": 1, "min_count": 1, "networks": [{"uuid": "e7c90970-c304-4f51-9d65-4be42318487c"}], "security_groups": [{"name": "default"}]}}'
**********************************************************************************
We are going to initiate REST API POST requests creating servers been
issued via Chrome Advanced REST Client
**********************************************************************************
[root@ip-192-169-142-54 ~(keystone_demo)]# glance image-list
+--------------------------------------+-----------------------+
| ID | Name |
+--------------------------------------+-----------------------+
| 28b590fa-05c8-4706-893a-54efc4ca8cd6 | cirros |
| 9c78c3da-b25b-4b26-9d24-514185e99c00 | Ubuntu1510Cloud-image |
| a050a122-a1dc-40d0-883f-25617e452d90 | VF23Cloud-image |
+--------------------------------------+-----------------------+
[root@ip-192-169-142-54 ~(keystone_demo)]# neutron net-list
+--------------------------------------+--------------+----------------------------------------+
| id | name | subnets |
+--------------------------------------+--------------+----------------------------------------+
| 43daa7c3-4e04-4661-8e78-6634b06d63f3 | public | 71e0197b-fe9a-4643-b25f-65424d169492 |
| | | 192.169.142.0/24 |
| 292a2f21-70af-48ef-b100-c0639a8ffb22 | demo_network | d7aa6f0f-33ba-430d-a409-bd673bed7060 |
| | | 50.0.0.0/24 |
+--------------------------------------+--------------+----------------------------------------+
First required Headers were created in corresponding fields and
following fragment was placed in Raw Payload area of Chrome Client
{"server":
{"name": "VF23Devs03",
"key_name" : "oskeymitaka0420",
"imageRef" : "a050a122-a1dc-40d0-883f-25617e452d90",
"flavorRef": "2",
"max_count": 1,
"min_count": 1,
"networks": [{"uuid": "292a2f21-70af-48ef-b100-c0639a8ffb22"}],
"security_groups": [{"name": "default"}]
}
}
Now create a couple of servers Fedora23 and Ubuntu 15.10 via Chrome Advanced REST Client GUI interface
***************************************************************************************
Re-launch Chrome REST Client again for servers verification via GET request
***************************************************************************************
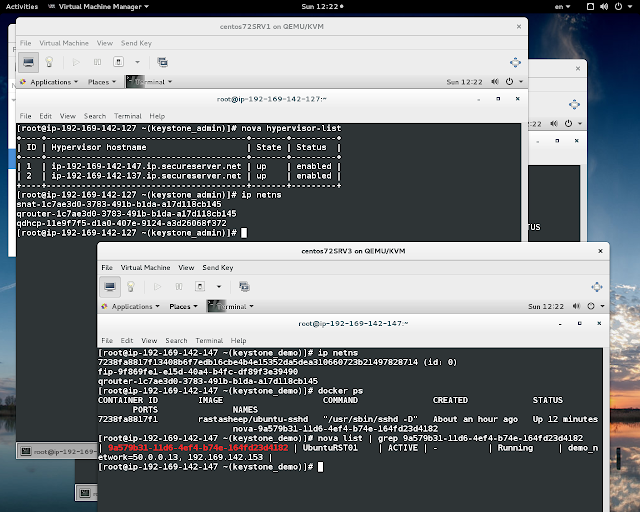
Just in case run `nova list`
successfully issuing REST API POST requests for creating RDO Mitaka Servers (VMs) as well as getting information about servers via GET requests.
All required HTTP Headers are configured in GUI environment as well as
body request field for servers creation.
Version of keystone API installed v2.0
Following [ 1 ] to authenticate access to OpenStack Services, you are supposed first of all to issue an authentication request to get authentication token. If the request succeeds, the server returns an authentication token.
Source keystonerc_demo on Controller or on Compute node. It doesn't
matter. Then run this cURL command to request a token:
curl -s -X POST http://192.169.142.54:5000/v2.0/tokens \
-H "Content-Type: application/json" \
-d '{"auth": {"tenantName": "'"$OS_TENANT_NAME"'", "passwordCredentials": {"username": "'"$OS_USERNAME"'", "password": "'"$OS_PASSWORD"'"}}}' \
| python -m json.tool
to get authentication token and scroll down to the bottom :-
"token": {
"audit_ids": [
"ce1JojlRSiO6TmMTDW3QNQ"
],
"expires": "2016-04-21T18:26:28Z",
"id": "0cfb3ec7a10c4f549a3dc138cf8a270a", <== X-Auth-Token
"issued_at": "2016-04-21T17:26:28.246724Z",
"tenant": {
"description": "default tenant",
"enabled": true,
"id": "1578b57cfd8d43278098c5266f64e49f", <== Demo tenant's id
"name": "demo"
}
},
"user": {
"id": "8e1e992eee474c3ab7a08ffde678e35b",
"name": "demo",
"roles": [
{
"name": "heat_stack_owner"
},
{
"name": "_member_"
}
],
"roles_links": [],
"username": "demo"
}
}
}
*****************************************************************************************************
Original request to obtain token might be issued via Chrome Advanced REST Client as well
*****************************************************************************************************

Scrolling down shows up token been returned and demo's tenant id

Required output
{
"access":
{
"token":
{
"issued_at": "2016-04-21T21:56:52.668252Z"
"expires": "2016-04-21T22:56:52Z"
"id": "dd119ea14e97416b834ca72aab7f8b5a"
"tenant":
{
"description": "default tenant"
"enabled": true
"id": "1578b57cfd8d43278098c5266f64e49f"
"name": "demo"
}
*****************************************************************************
Next create ssh-keypair via CLI or dashboard for particular tenant :-
*****************************************************************************
nova keypair-add oskeymitaka0417 > oskeymitaka0417.pem
chmod 600 *.pem
******************************************************************************************************
Following bellow is a couple of samples REST API POST requests starting servers as they are usually described and issued ( [ 2 ] )
******************************************************************************************************
curl -g -i -X POST http://192.169.142.54:8774/v2/1578b57cfd8d43278098c5266f64e49f/servers -H "User-Agent: python-novaclient" -H "Content-Type: application/json" -H "Accept: application/json" -H "X-Auth-Token: 0cfb3ec7a10c4f549a3dc138cf8a270a" -d '{"server": {"name": "CirrOSDevs03", "key_name" : "oskeymitaka0417", "imageRef": "2e148cd0-7dac-49a7-8a79-2efddbd83852", "flavorRef": "1", "max_count": 1, "min_count": 1, "networks": [{"uuid": "e7c90970-c304-4f51-9d65-4be42318487c"}], "security_groups": [{"name": "default"}]}}'
curl -g -i -X POST http://192.169.142. 54:8774/v2/1578b57cfd8d43278098c5266f64e49f/servers -H "User-Agent: python-novaclient" -H "Content-Type: application/json" -H "Accept: application/json" -H "X-Auth-Token: 0cfb3ec7a10c4f549a3dc138cf8a270a" -d '{"server": {"name": "VF23Devs03", "key_name" : "oskeymitaka0417", "imageRef": "5b00b1a8-30d1-4e9d-bf7d-5f1abed5173b", "flavorRef": "2", "max_count": 1, "min_count": 1, "networks": [{"uuid": "e7c90970-c304-4f51-9d65-4be42318487c"}], "security_groups": [{"name": "default"}]}}'
**********************************************************************************
We are going to initiate REST API POST requests creating servers been
issued via Chrome Advanced REST Client
**********************************************************************************
[root@ip-192-169-142-54 ~(keystone_demo)]# glance image-list
+--------------------------------------+-----------------------+
| ID | Name |
+--------------------------------------+-----------------------+
| 28b590fa-05c8-4706-893a-54efc4ca8cd6 | cirros |
| 9c78c3da-b25b-4b26-9d24-514185e99c00 | Ubuntu1510Cloud-image |
| a050a122-a1dc-40d0-883f-25617e452d90 | VF23Cloud-image |
+--------------------------------------+-----------------------+
[root@ip-192-169-142-54 ~(keystone_demo)]# neutron net-list
+--------------------------------------+--------------+----------------------------------------+
| id | name | subnets |
+--------------------------------------+--------------+----------------------------------------+
| 43daa7c3-4e04-4661-8e78-6634b06d63f3 | public | 71e0197b-fe9a-4643-b25f-65424d169492 |
| | | 192.169.142.0/24 |
| 292a2f21-70af-48ef-b100-c0639a8ffb22 | demo_network | d7aa6f0f-33ba-430d-a409-bd673bed7060 |
| | | 50.0.0.0/24 |
+--------------------------------------+--------------+----------------------------------------+
First required Headers were created in corresponding fields and
following fragment was placed in Raw Payload area of Chrome Client
{"server":
{"name": "VF23Devs03",
"key_name" : "oskeymitaka0420",
"imageRef" : "a050a122-a1dc-40d0-883f-25617e452d90",
"flavorRef": "2",
"max_count": 1,
"min_count": 1,
"networks": [{"uuid": "292a2f21-70af-48ef-b100-c0639a8ffb22"}],
"security_groups": [{"name": "default"}]
}
}
Now create a couple of servers Fedora23 and Ubuntu 15.10 via Chrome Advanced REST Client GUI interface
***************************************************************************************
Re-launch Chrome REST Client again for servers verification via GET request
***************************************************************************************
Just in case run `nova list`